Achievement
The Internet, although extremely robust, is notoriously vulnerable to attack by means of the Border Gateway Protocol (BGP). BGP update messages are assumed to be trustworthy. In other words, the reachability information shared between autonomous systems (ASes) is assumed to be correct without any verification. Despite the fact that the latest version of the BGP protocol was released in 2006, there are no inherent protection mechanisms against participants advertising false routes.
In practice, BGP lacks authentication mechanisms not only for the announcement of the origin of IP prefixes but also the paths to that prefix. This leaves BGP vulnerable to unintended misconfiguration and malicious attacks. The results of these disruptions include traffic blackholing and traffic interception. In traffic blackholing, the network traffic is dropped, never reaching its destination. In traffic interception, the announcing AS reroutes traffic for the victim IP prefix and redirects it to the original origin AS after interception. On this misdirected route, the traffic may be subject to eavesdropping, traffic analysis, or tampering.
Here, we propose an anomaly detection method that aims to identify incipient incidents before diffusion and harm by identifying a routing event as it emerges. Our goal is to identify anomalous routing events as soon as possible with respect to manually verified ground truth metadata, such as BGPMon, Oracle Dyn, and Ars Technica. Our ground truth sources manually investigate these incidents and determine its impact based on empirical measurements. A similar procedure has been used before for labeling purposes. To do this, we use control-plane data collected by RouteViews and served by BGPStream. The key observation in our anomaly detection method is that there are bursty BGP announcements as soon as new routes are adopted by neighbor ASes. We characterize bursty announcements through statistical analysis of inter-arrival times. We conduct a casebased systematic analysis of the changes of inter-arrival times that are associated with well-known anomalous events that resulted in traffic blackholing and intersection. We then propose a method based on control-plane information and statistical analysis to detect anomalous BGP announcements. We show that the proposed method is able to correctly identify the incidents in agreement with the ground truth while reducing significantly the number of false positives when compared with the volume baseline.
Significance and Impact
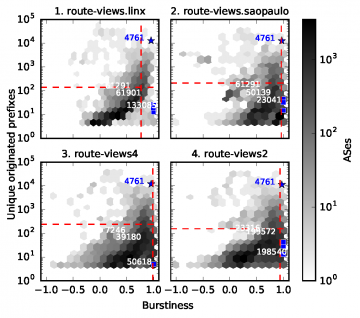
- We validate our conjecture that inter-arrival time patterns of BGP announcements are a useful signature for identification of BGP routing incidents. We show that bursty patterns of announcements are noticeable in agreement with the manually verified ground truth metadata. To do so, we quantify the burstiness of BGP announcements by observing that when there are BGP incidents, there are groups of announcements with short inter-arrival times followed by larger ones. We report that this observation is independent of the volume of announcements.
- We describe the design of a proof-of-concept BGP anomaly detection method that uses data only from current route collectors. We use RouteViews route collectors to compute a detection signature of BGP incidents based on the impact of short inter-arrival times.
- We report results of a longitudinal analysis of large-scale routing incidents. We evaluated the proposed method by studying four different BGP incidents that resulted in blackholing, i.e., Indosat in April 2014, Telecom Malaysia in June 2015, Bharti Airtel Ltd. in November 2015, and MainOne in November 2018; and three additional incidents that resulted in traffic interception, i.e., GlobalOneBell in February 2013, Opin Kerfi in July 2013, and Rostelecom in April 2017. Our approach allows for statistically significant differentiation between normal behavior and disruption or anomalous changes during the incidents. We validate this by conducting Monte Carlo simulations on the burstiness behavior of ASes. We show that the proposed method outperforms, in most cases, the performance achieved by the baseline of volume of announcements in terms of false positives and negatives.
Research Details
We illustrate the efficacy of leveraging RouteViews collectors’ infrastructure to identify anomalous routing incidents through the analysis of inter-arrival times of announcements. As a complement to current anomaly identification approaches, we have demonstrated a proof-of-concept that identifies real hijack incidents when these were detected in practice by leveraging the current RouteViews collectors’ infrastructure. We have characterized seven different incidents, including, large-scale and for traffic interception purposes from a different perspective, one derived by analyzing the patterns of burstiness of BGP announcements. The method detailed in this paper relies on the fact that large-scale disruption events produces groups of BGP announcements of relatively high frequency followed by periods of relatively infrequent events, which can be measured as burstiness. Relying on this observation, we describe a detection method that is able to indicate, from a collector point of view, when an incident is incipient.
Publication:
P. Moriano, R. Hill, and L. J. Camp. Using bursty announcements for detecting BGP routing anomalies. Computer Networks, vol. 188, p. 107835, 2021. DOI: 10.1016/J.COMNET.2021.107835
Last Updated: February 1, 2021 - 3:05 pm